Subscriber Access Manager
SAM helps identify and eliminate cloned radios
Most likely, cloned radios are consuming valuable airtime on your two-way communications network. Days and weeks may be spent tracking down the source.
- How many cloned radios exist on the system?
- Are hackers doing more than just eavesdropping?
- Who is stealing airtime?
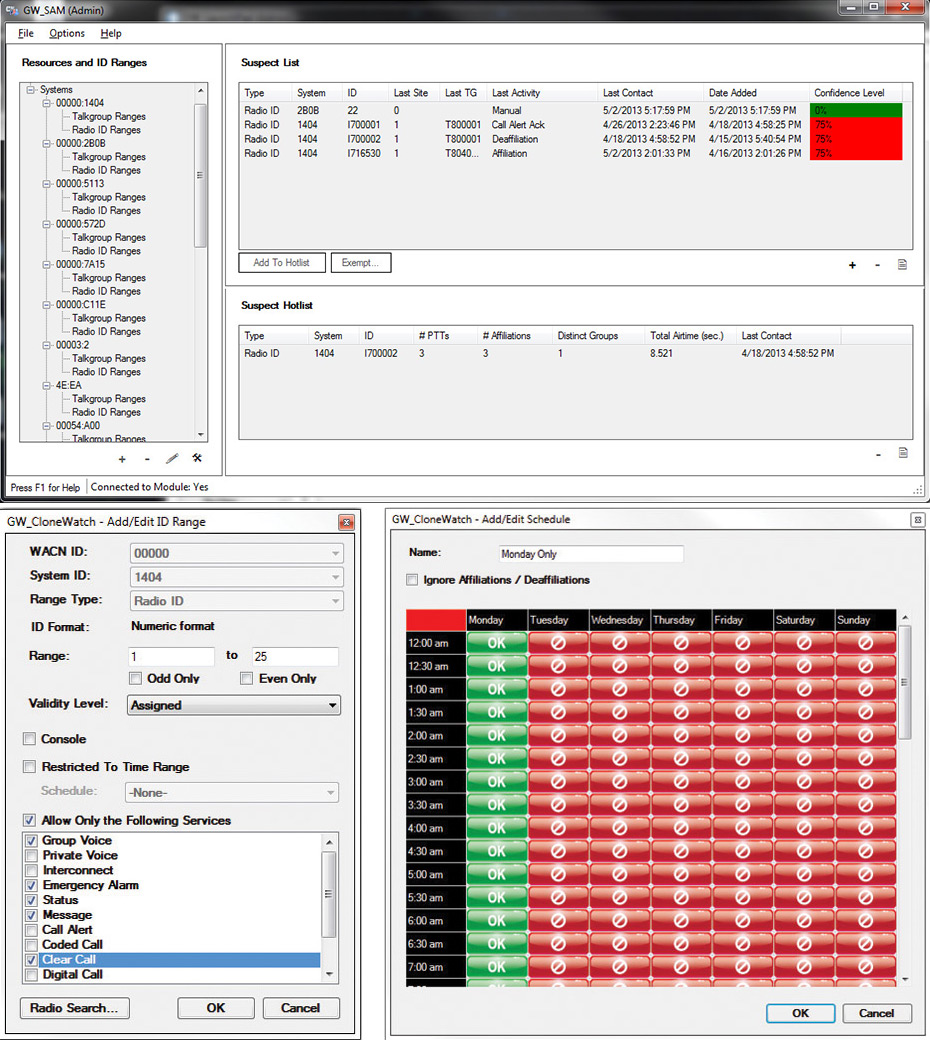
SAM monitors talkgroups and radios for suspicious activity. A suspect is a resource (radio ID or group) that breaks a predefined rule or expected behavior. Suspect resources are added to a list where the suspect’s activities are then displayed and recorded in detail.
When an activity (e.g., PTT, affiliation, etc.) is received on a group or radio ID — also known as resources — this activity is validated against the Resource Ranges defined within the SAM interface. If the activity of the resource violates the expected activity definitions, the resource is added to the Suspect List. Once in the Suspect List, the resource’s activity is closely monitored and detailed in the SAM database.
Features At A Glance
- Dynamically adds suspected cloned radios to the Suspect List, based upon violations.
- Alert is issued when a unit is added to the Suspect List.
- Suspects are organized into the Suspect List. The list is sorted on many suspect properties and shows printable, real-time information on its suspects.
- Suspects can be echoed in a Suspect Hot List which shows additional details on a suspect.
- Suspects can be marked as Exempt.
- SAM-related resources are displayed out in an organized tiered tree structure.
- Screen space is optimized with collapsible screen partitions.
- Talkgroup and unit ID values are organized in ranges for quick data entry.